
You are in a maze of twisty little passages, all alike...
A Month of Bans: A Cybersecurity Review
November 7, 2024 Reading time: 33 minutes
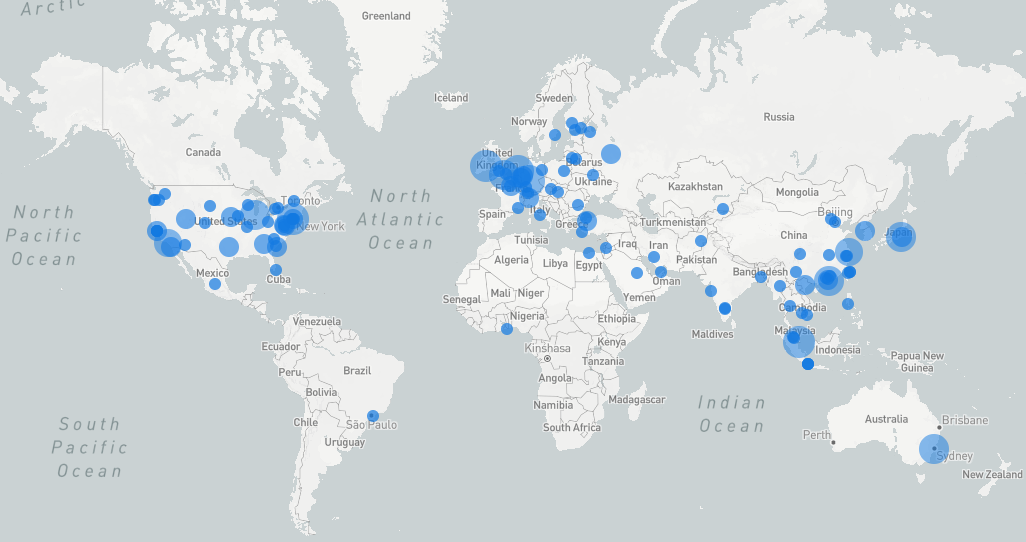
If you've ever maintained a public internet server, either as a hobby or as a job, you're no stranger to random probes and port-scans from evildoers looking for trouble. You've seen brute force attempts to log in to servers or email accounts, probes for vulnerable web services, SYN floods, spammers checking for open relays, and many other attacks. If your server is on the internet, it's a target. Many hobbyist and small business systems administrators use Fail2Ban to respond to these threats. Fail2Ban is an always-vigilant process that monitors system logs and responds to perceived attacks by temporarily blocking the attacker's IP address at the firewall level.
Fail2Ban has served me well, but I wanted to gain some additional insight into the origins and behaviors of the villains behind the attacks. During the month of October, I used a custom Fail2Ban script to collect geolocation and other data about each IP address that Fail2Ban identified as malicious on three hosts, including 2 web servers and a mail server. Here are the results.
Read more
Fail2Ban Demystified: Custom Fail2Ban Actions
October 1, 2024 Reading time: 33 minutes
Fail2Ban is a powerful security tool that bridges your public-facing network services (ssh, mail server, web server, etc.) and your firewall. The Fail2Ban daemon constantly monitors your server logs, looking for troublemakers. When an intruder or suspicious activity is detected, it takes action! By default, Fail2Ban writes a temporary firewall rule that blocks the offender’s IP address on selected ports for a short period of time.
The real power in Fail2Ban, though, lies in its customizability. Using custom action scripts, admins can configure how Fail2Ban responds to threats, extending its abilities far beyond simply interfacing with the firewall. For example, you can define actions that will send an email or notification, write to a log file or database, invoke a web API, react differently in different contexts, and so on. The possibilities are unlimited!
This article explains how actions in Fail2Ban are defined and customized so that you can get the most out of Fail2Ban.
Read more
🪛 📐 TOOLBOX 🔨 🔧
📬 SPF Record WizardThe spell trickles away to nothing. The merchant smiles. "Do you think you are the first magician to try to use lawless, thieving magic on a humble merchant?" He throws you into the street and bars the door.