
You are in a maze of twisty little passages, all alike...

The Worst Passwords of 2024?
November 15, 2024 Reading time: 17 minutes
NordPass has published their 2024 list of the 200 most commonly-used passwords and, apparently, many people still haven't gotten the memo about password security. Is one of your passwords on this year's list? Well, probably not. NordPass' data comes from a large database of passwords, presumably passwords that have been made public after online service data breaches. A closer look at the data gives some interesting insights into both the psychology behind passwords and websites' adherence to security "best practices." But it also raises some questions about the methodology NordPass used to generate the list. The closer I looked at NordPass' annual list, the more questions I had.
This year, NordPass' crown of dishonor goes to "123456" as the world's most common password in 2024. But is it really? In this article, I'll take a look at NordPass' data, which may not be quite what's on the label, and, just for fun, I'll compare it to some recent password data of my own, collected originally for my recent A Month of Bans article.
Read more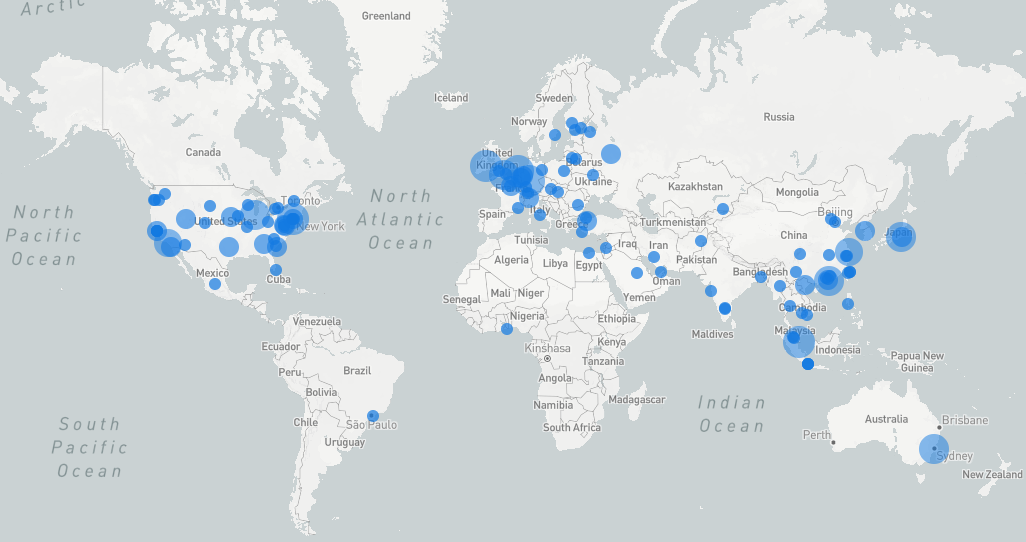
A Month of Bans: A Cybersecurity Review
November 7, 2024 Reading time: 33 minutes
If you've ever maintained a public internet server, either as a hobby or as a job, you're no stranger to random probes and port-scans from evildoers looking for trouble. You've seen brute force attempts to log in to servers or email accounts, probes for vulnerable web services, SYN floods, spammers checking for open relays, and many other attacks. If your server is on the internet, it's a target. Many hobbyist and small business systems administrators use Fail2Ban to respond to these threats. Fail2Ban is an always-vigilant process that monitors system logs and responds to perceived attacks by temporarily blocking the attacker's IP address at the firewall level.
Fail2Ban has served me well, but I wanted to gain some additional insight into the origins and behaviors of the villains behind the attacks. During the month of October, I used a custom Fail2Ban script to collect geolocation and other data about each IP address that Fail2Ban identified as malicious on three hosts, including 2 web servers and a mail server. Here are the results.
Read more
Updating nftables with DDNS
October 9, 2024 Reading time: 18 minutes
Hobbyist admins and home-labbers sometimes want to make services on a remote host available to machines on a home network. Unfortunately, many residential ISP customers are stuck with dynamic IP addresses, even when they're not behind a CGNAT. This makes securing the remote host difficult. You'd like to configure the remote firewall to allow traffic only from friendly IP addresses, but if one or more of your addresses might change at any time, what can you do? One option is to buy a fixed IP address from your ISP, but that can be costly.
This article describes how you can configure a remote server using nftables to automatically update its firewall rules so that dynamic IP traffic is allowed with minimal downtime when the IP address changes. The solution requires making a small change to your nftables configuration and a short script that runs periodically as a cron job.
Read more
Fail2Ban Demystified: Custom Fail2Ban Actions
October 1, 2024 Reading time: 33 minutes
Fail2Ban is a powerful security tool that bridges your public-facing network services (ssh, mail server, web server, etc.) and your firewall. The Fail2Ban daemon constantly monitors your server logs, looking for troublemakers. When an intruder or suspicious activity is detected, it takes action! By default, Fail2Ban writes a temporary firewall rule that blocks the offender’s IP address on selected ports for a short period of time.
The real power in Fail2Ban, though, lies in its customizability. Using custom action scripts, admins can configure how Fail2Ban responds to threats, extending its abilities far beyond simply interfacing with the firewall. For example, you can define actions that will send an email or notification, write to a log file or database, invoke a web API, react differently in different contexts, and so on. The possibilities are unlimited!
This article explains how actions in Fail2Ban are defined and customized so that you can get the most out of Fail2Ban.
Read morePostfix Demystified: Incoming Mail Restrictions
September 24, 2024 Reading time: 40 minutes
 There was a time in the early days of the internet when spam, phishing, CEO impersonation, email trojans, and other forms of email abuse were not a thing. Mail servers would happily accept mail from any domain and forward it along to any other domain with no worry of being an unwitting accomplice in evildoing. Alas, those blissful days are long gone and, today, a mail server’s incoming mail policy is a critical early line of defense against these threats.
There was a time in the early days of the internet when spam, phishing, CEO impersonation, email trojans, and other forms of email abuse were not a thing. Mail servers would happily accept mail from any domain and forward it along to any other domain with no worry of being an unwitting accomplice in evildoing. Alas, those blissful days are long gone and, today, a mail server’s incoming mail policy is a critical early line of defense against these threats.
In this article, you will learn how to configure Postfix to enforce a simple mail acceptance policy for your domain(s). Your policy is determined by the role(s) your server will play (relay, destination, send-only, etc.), where your users typically connect from, and your tolerance for spam and misbehaving mail clients, among other considerations.
Read more
🪛 📐 TOOLBOX 🔨 🔧
📬 SPF Record WizardThe computer sounds surly. "I told you to buy those additional I/O options. You know as well as I do that I can't talk to that stupid mass detector, so you'll just have to tell me the coordinates from its output. Maybe next time you'll listen."