
You are in a maze of twisty little passages, all alike...

SPF Demystified: The Complete Guide to SPF Records
December 12, 2024 Reading time: 43 minutes
Whether you host your own mail server or you outsource your email needs, if your domain sends even a small amount of email, you need a robust, accurate SPF record. Your SPF record helps protect your domain's reputation by making it more difficult for spammers, phishers, and other evildoers to spoof email from your domain. When you publish an SPF record, you let other mail servers know exactly which hosts are allowed to send mail for your domain, and which are not. Large email services may even refuse mail from domains with a missing or invalid SPF record, tightening their stranglehold on email. And, unfortunately, even a small error in your SPF record can make it invalid, resulting in bounced or lost outgoing mail for your domain. It's important that you get your SPF record right.
This guide provides a detailed explanation and several examples to help you understand SPF: what it does, how it works, and how to build a suitable SPF record. If you just need a quick solution, though, our SPF Record Wizard can walk you through the process, check for common mistakes, and suggest an SPF record for your domain, suitable for copy-pasting into a DNS TXT record.
Read more
The Worst Passwords of 2024?
November 15, 2024 Reading time: 17 minutes
NordPass has published their 2024 list of the 200 most commonly-used passwords and, apparently, many people still haven't gotten the memo about password security. Is one of your passwords on this year's list? Well, probably not. NordPass' data comes from a large database of passwords, presumably passwords that have been made public after online service data breaches. A closer look at the data gives some interesting insights into both the psychology behind passwords and websites' adherence to security "best practices." But it also raises some questions about the methodology NordPass used to generate the list. The closer I looked at NordPass' annual list, the more questions I had.
This year, NordPass' crown of dishonor goes to "123456" as the world's most common password in 2024. But is it really? In this article, I'll take a look at NordPass' data, which may not be quite what's on the label, and, just for fun, I'll compare it to some recent password data of my own, collected originally for my recent A Month of Bans article.
Read more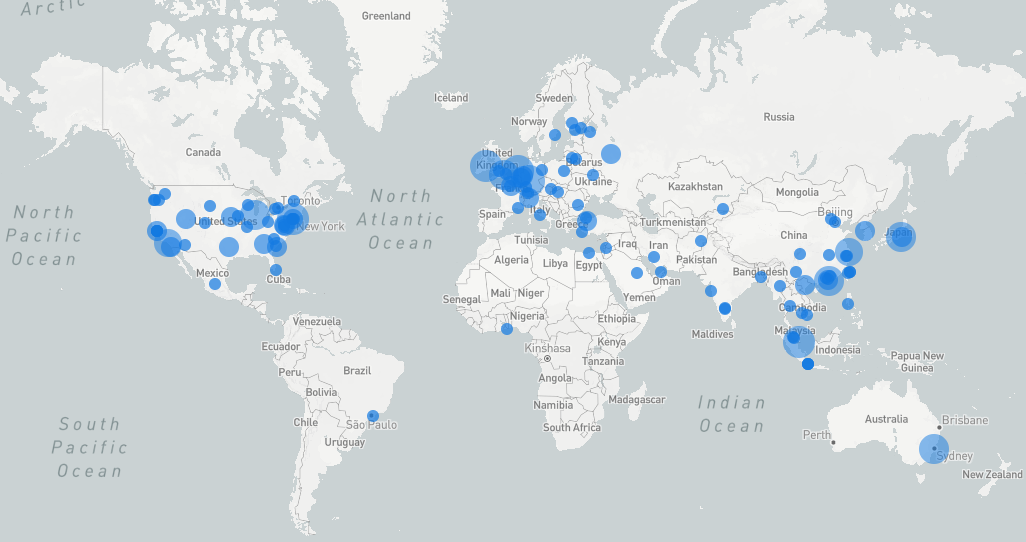
A Month of Bans: A Cybersecurity Review
November 7, 2024 Reading time: 33 minutes
If you've ever maintained a public internet server, either as a hobby or as a job, you're no stranger to random probes and port-scans from evildoers looking for trouble. You've seen brute force attempts to log in to servers or email accounts, probes for vulnerable web services, SYN floods, spammers checking for open relays, and many other attacks. If your server is on the internet, it's a target. Many hobbyist and small business systems administrators use Fail2Ban to respond to these threats. Fail2Ban is an always-vigilant process that monitors system logs and responds to perceived attacks by temporarily blocking the attacker's IP address at the firewall level.
Fail2Ban has served me well, but I wanted to gain some additional insight into the origins and behaviors of the villains behind the attacks. During the month of October, I used a custom Fail2Ban script to collect geolocation and other data about each IP address that Fail2Ban identified as malicious on three hosts, including 2 web servers and a mail server. Here are the results.
Read more
A 3-2-1(-1-0) Backup Plan for Your Synology NAS
November 3, 2024 Reading time: 43 minutes
It’s late at night and Raul is frantic. He’s desperately searching for an important electronic document he needs for work. He knows it’s on his NAS somewhere, but he can’t remember where he saved it. His frown deepens as he opens folder after folder, not finding what he needs. Then his blood runs cold as he remembers deleting a swath of “unneeded” files last week as part of his annual Spring cleaning. And he has no recent backup. He’d been meaning to back up his NAS, but he kept telling himself he’d do it later.
Raul wakes in a cold sweat. It was all a bad dream. Whew! To reassure himself, and vowing to back up his data right now, Raul gets up and boots his computer. But he realizes all is not well as the computer finishes booting:
Read more
I Won 9.8 Million Dollars from PCH?
October 15, 2024 Reading time: 17 minutes
I don't live in the US, but I do have a US-based phone number for business. The number gets a never-ending stream of spam SMS (text messages) from area codes far and wide warning me about cash due on packages I never ordered, inviting me to "spicy parties," and alerting me that members of my HOTLIST (whatever that is) are active now. Occasionally I'll get a call from a number I don't recognize and I just let it go to voice mail. Recently, I learned just how lucky I am when I got this message:
"Hello. My name is "David Green" and I'm calling from the Publishers Clearing House in regards to you being the second place lucky winner. Of 9.8 million dollars. Please give me a call back at 810-204-8927. Thank you."
Read more

Updating nftables with DDNS
October 9, 2024 Reading time: 18 minutes
Hobbyist admins and home-labbers sometimes want to make services on a remote host available to machines on a home network. Unfortunately, many residential ISP customers are stuck with dynamic IP addresses, even when they're not behind a CGNAT. This makes securing the remote host difficult. You'd like to configure the remote firewall to allow traffic only from friendly IP addresses, but if one or more of your addresses might change at any time, what can you do? One option is to buy a fixed IP address from your ISP, but that can be costly.
This article describes how you can configure a remote server using nftables to automatically update its firewall rules so that dynamic IP traffic is allowed with minimal downtime when the IP address changes. The solution requires making a small change to your nftables configuration and a short script that runs periodically as a cron job.
Read more
🪛 📐 TOOLBOX 🔨 🔧
📬 SPF Record WizardJeearr is vanquished; the kingdom is saved. But you - you are stranded in a land unknown, and your closest friend, the greatest Enchanter of his age, lies dead by your own hand. Kneeling by his blood-soaked corpse, you beg for another chance...